Internal developer platform made easy

What is HCP Waypoint?
HCP Waypoint lets platform teams define golden patterns and workflows for developers to manage applications at scale.
Learn more about HCP Waypoint
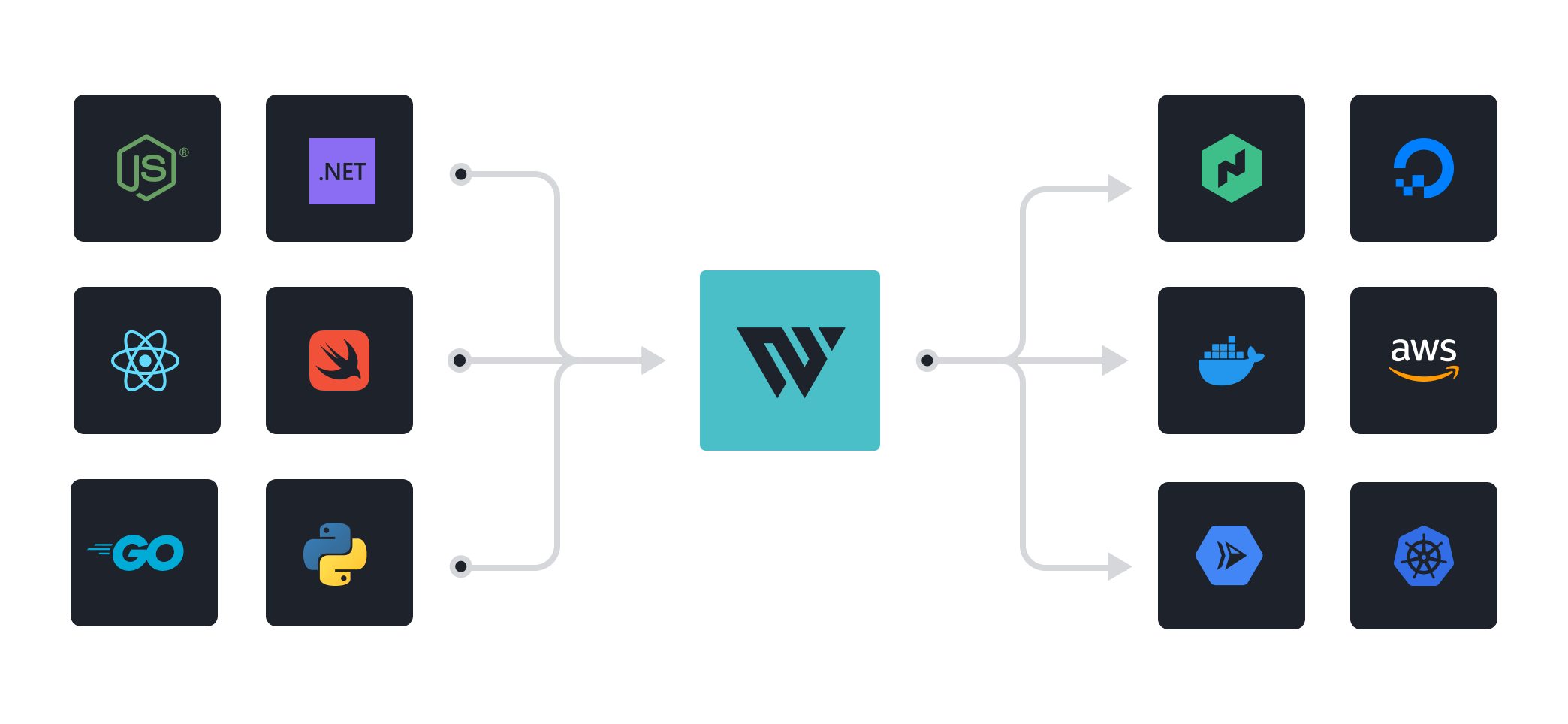


HCP Waypoint lets platform teams define golden patterns and workflows for developers to manage applications at scale.

